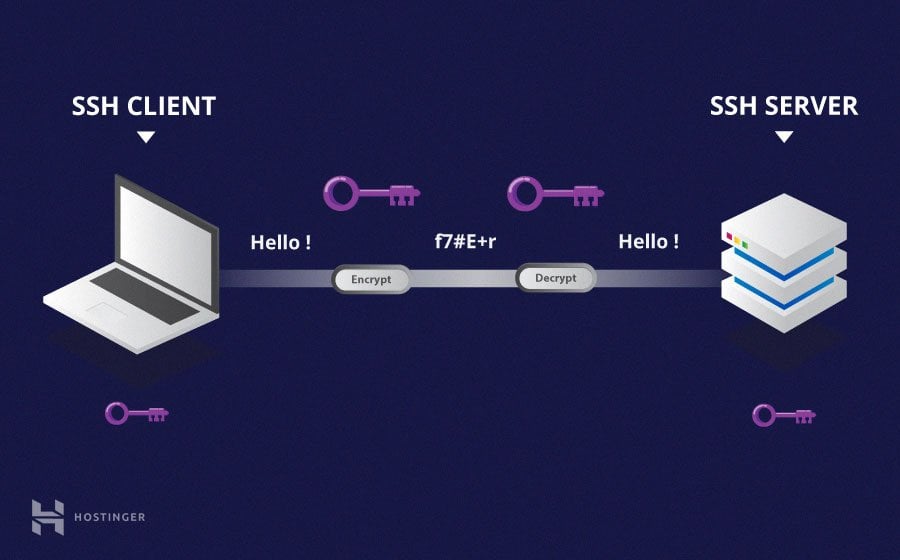
SSH (Secure Shell) has become a cornerstone for securely accessing and managing remote IoT devices. In today's interconnected world, IoT devices are increasingly integrated into our daily lives, from smart homes to industrial automation systems. Ensuring secure communication between these devices and their controllers is critical to protecting sensitive data and maintaining system integrity.
As the number of IoT devices grows exponentially, so does the need for secure methods to manage them remotely. SSH provides a robust solution by encrypting all data exchanged between a client and server, making it an essential tool for anyone working with IoT technology. This tutorial will guide you step-by-step on how to set up and use SSH for remote IoT device management.
Whether you're a beginner or an experienced developer, this guide will equip you with the knowledge and tools necessary to ensure your IoT devices remain secure and accessible from anywhere in the world. Let's dive into the world of SSH and IoT!
Read also:Vegamoviesin Your Ultimate Destination For Streaming Movies
Table of Contents
- Introduction to SSH
- IoT and Remote Access
- Why Choose SSH?
- Setting Up SSH
- Connecting to a Remote IoT Device
- Securing Your SSH Connection
- Troubleshooting SSH Issues
- Advanced SSH Features
- Best Practices for SSH
- Conclusion and Next Steps
Introduction to SSH
SSH, or Secure Shell, is a network protocol designed to provide secure communication over unsecured networks. It encrypts all data transmitted between a client and a server, ensuring that sensitive information, such as passwords and commands, cannot be intercepted by malicious actors. Developed in the mid-1990s, SSH has become the go-to solution for secure remote access, particularly in environments where security is paramount.
SSH operates on port 22 by default and supports various authentication methods, including passwords and public-key cryptography. Its versatility makes it suitable for a wide range of applications, from remote command execution to file transfer using SFTP (Secure File Transfer Protocol).
With the rise of IoT, SSH has become an indispensable tool for managing remote devices securely. Whether you're configuring a smart thermostat or monitoring industrial sensors, SSH ensures that your interactions with these devices remain private and tamper-proof.
IoT and Remote Access
The Internet of Things (IoT) has revolutionized the way we interact with the world around us. From smart home devices to industrial automation systems, IoT devices are transforming industries and improving our quality of life. However, with this increased connectivity comes the challenge of managing these devices remotely while maintaining security.
Remote access to IoT devices is essential for troubleshooting, configuration, and monitoring. Without secure access protocols, these devices become vulnerable to attacks, potentially compromising sensitive data and system integrity. This is where SSH comes into play, offering a secure and reliable method for remote device management.
Read also:Maplestory The Ultimate Guide To Exploring The World Of Maplestory
By leveraging SSH, organizations can ensure that their IoT devices remain accessible and secure, regardless of their location. This tutorial will walk you through the process of setting up and using SSH for remote IoT device management, providing you with the tools and knowledge necessary to protect your devices.
Why Choose SSH?
When it comes to securing remote access to IoT devices, SSH stands out as the preferred solution for several reasons:
- Encryption: SSH encrypts all data transmitted between the client and server, ensuring that sensitive information remains confidential.
- Authentication: SSH supports multiple authentication methods, including public-key cryptography, which provides a higher level of security compared to traditional password-based authentication.
- Reliability: SSH is a mature and widely adopted protocol, with implementations available for virtually every operating system and platform.
- Flexibility: SSH can be used for a variety of tasks, including remote command execution, file transfer, and tunneling, making it a versatile tool for managing IoT devices.
By choosing SSH, you can ensure that your IoT devices remain secure and accessible, protecting both your data and your systems from potential threats.
Setting Up SSH
Installing SSH
Before you can use SSH to manage your IoT devices, you need to install an SSH server on the device and an SSH client on your local machine. Most Linux-based IoT devices come with SSH pre-installed, but if not, you can install it using the following command:
For Debian-based systems:
sudo apt-get update
sudo apt-get install openssh-server
For Red Hat-based systems:
sudo yum install openssh-server
Once installed, start the SSH service and enable it to start on boot:
sudo systemctl start ssh
sudo systemctl enable ssh
Configuring SSH
After installing SSH, you should configure it to meet your specific needs. The SSH configuration file is located at /etc/ssh/sshd_config. Open this file in a text editor and make the following changes:
- Port: Change the default port (22) to a non-standard port to reduce the risk of brute-force attacks.
- PermitRootLogin: Set this to "no" to disable root login, enhancing security.
- PasswordAuthentication: Set this to "no" to disable password-based authentication and enforce the use of SSH keys.
After making these changes, restart the SSH service to apply them:
sudo systemctl restart ssh
Connecting to a Remote IoT Device
Once SSH is set up on your IoT device, you can connect to it from your local machine using an SSH client. On most Unix-based systems, the SSH client is pre-installed. To connect, simply open a terminal and enter the following command:
ssh username@ip_address
Replace "username" with the username on the IoT device and "ip_address" with the device's IP address. If you changed the default port, include it in the command as follows:
ssh -p port_number username@ip_address
Upon successful connection, you will be prompted to enter your SSH key or password, depending on your configuration. Once authenticated, you will have secure access to your IoT device.
Securing Your SSH Connection
Using SSH Keys
One of the most effective ways to secure your SSH connection is by using SSH keys. SSH keys provide a more secure and convenient method of authentication compared to passwords. To generate an SSH key pair, use the following command:
ssh-keygen -t rsa -b 4096
This will create a private and public key pair. Copy the public key to your IoT device using the ssh-copy-id command:
ssh-copy-id username@ip_address
Now, when you connect to the device, you will be authenticated using your SSH key instead of a password.
Disabling Password Authentication
To further enhance security, you should disable password authentication and enforce the use of SSH keys. To do this, edit the SSH configuration file (/etc/ssh/sshd_config) and set the following option:
PasswordAuthentication no
Restart the SSH service to apply the changes:
sudo systemctl restart ssh
Troubleshooting SSH Issues
While SSH is a reliable protocol, issues may arise from time to time. Below are some common problems and their solutions:
- Connection Refused: Ensure that the SSH service is running and that the correct port is specified in the connection command.
- Authentication Failed: Verify that your SSH key is correctly installed on the IoT device and that password authentication is disabled if using keys.
- Timeout Errors: Check the network connection between your local machine and the IoT device, ensuring that no firewalls or routers are blocking the SSH port.
If you encounter persistent issues, consult the SSH logs for more detailed information:
sudo journalctl -u ssh
Advanced SSH Features
Beyond basic remote access, SSH offers several advanced features that can enhance your IoT management capabilities:
- Tunneling: Use SSH tunnels to securely access services running on your IoT device, such as web servers or databases.
- Port Forwarding: Forward specific ports from your local machine to the IoT device, enabling secure access to internal services.
- SSH Agent Forwarding: Allow your IoT device to use your local SSH keys for authentication, simplifying access to other remote systems.
These features can significantly improve the functionality and security of your IoT setup, providing you with greater control over your devices.
Best Practices for SSH
To ensure the security and reliability of your SSH connections, follow these best practices:
- Regularly Update SSH: Keep your SSH server and client software up to date to protect against known vulnerabilities.
- Use Strong SSH Keys: Generate SSH keys with sufficient bit lengths (e.g., 4096 bits) and protect them with strong passphrases.
- Monitor Logs: Regularly review SSH logs for signs of unauthorized access attempts or suspicious activity.
By adhering to these best practices, you can maintain a secure and efficient SSH environment for managing your IoT devices.
Conclusion and Next Steps
In this tutorial, we've explored the world of SSH and its role in securing remote access to IoT devices. From setting up SSH on your devices to implementing advanced security features, you now have the tools and knowledge necessary to protect your IoT setup. Remember to follow best practices and stay vigilant against potential threats.
We encourage you to share your thoughts and experiences in the comments section below. If you found this tutorial helpful, please consider sharing it with others who may benefit from it. For more in-depth guides and resources, explore our other articles on IoT security and management. Together, we can build a safer and more connected world!