In today's interconnected world, securing IoT devices through SSH login has become more critical than ever. As more users adopt smart devices, understanding how to download, install, and configure SSH on macOS is essential for maintaining robust cybersecurity. This guide will walk you through everything you need to know about SSH login for IoT devices and how to set it up on your Mac.
With the proliferation of IoT devices, ensuring their security is no longer optional but a necessity. Whether you're managing a home automation system or a small-scale industrial setup, SSH login offers a secure and reliable way to access and manage these devices remotely.
This article aims to provide comprehensive information on SSH login for IoT devices, including step-by-step instructions for downloading and setting it up on macOS. By the end of this guide, you'll have the tools and knowledge to secure your IoT devices effectively.
Read also:Best Remote Iot Control Revolutionizing The Way We Manage Devices
Table of Contents
- Introduction to SSH
- Why Securing IoT Devices Matters
- Understanding SSH for IoT Devices
- Step-by-Step SSH Setup on macOS
- Securing Your SSH Connection
- Common SSH Errors and Troubleshooting
- Best Practices for SSH Login in IoT
- SSH Alternatives for IoT Devices
- Frequently Asked Questions
- Conclusion: Secure Your IoT Devices with SSH
Introduction to SSH
Secure Shell (SSH) is a cryptographic protocol used to securely access remote devices over an unsecured network. Initially developed in the 1990s, SSH has become the standard for secure remote access. It provides a secure channel for data transmission, ensuring confidentiality, integrity, and authentication.
For IoT devices, SSH login is crucial as it allows administrators to manage devices remotely without compromising security. By encrypting all data exchanged between the client and server, SSH minimizes the risk of unauthorized access and data breaches.
SSH operates on port 22 by default and supports various authentication methods, including password-based and public key authentication. This flexibility makes SSH a versatile tool for securing IoT devices across different environments.
Why Securing IoT Devices Matters
The Internet of Things (IoT) has revolutionized the way we interact with technology, enabling smart homes, connected cars, and industrial automation. However, the rapid adoption of IoT devices has also exposed vulnerabilities that cybercriminals can exploit.
Unsecured IoT devices can become entry points for malicious actors to infiltrate networks, steal sensitive data, or launch large-scale attacks. According to a report by Symantec, the number of IoT attacks increased by 600% in 2022 alone. This alarming trend underscores the importance of securing IoT devices using protocols like SSH.
By implementing SSH login for IoT devices, users can significantly reduce the risk of unauthorized access and protect their networks from potential threats. This is particularly important for industries where data security and privacy are paramount.
Read also:Best Remote Iot Platform For Raspberry Pi Your Ultimate Guide
Understanding SSH for IoT Devices
SSH for IoT devices functions similarly to its traditional use in server management. However, there are specific considerations when applying SSH to IoT environments:
- Resource Constraints: Many IoT devices have limited processing power and memory, requiring lightweight SSH implementations.
- Authentication Methods: Public key authentication is often preferred over password-based authentication for IoT devices due to its higher security.
- Automation: SSH can be used to automate routine tasks on IoT devices, such as firmware updates and configuration changes.
Understanding these nuances is essential for effectively deploying SSH in IoT setups. By tailoring SSH configurations to the specific needs of IoT devices, users can ensure both security and functionality.
Step-by-Step SSH Setup on macOS
Install SSH on macOS
macOS comes pre-installed with OpenSSH, a widely used implementation of the SSH protocol. To verify that SSH is installed on your Mac, follow these steps:
- Open the Terminal application.
- Type the command
ssh -Vand press Enter. - If SSH is installed, the terminal will display the version number of OpenSSH.
If SSH is not installed, you can download and install it from the official OpenSSH website or use a package manager like Homebrew.
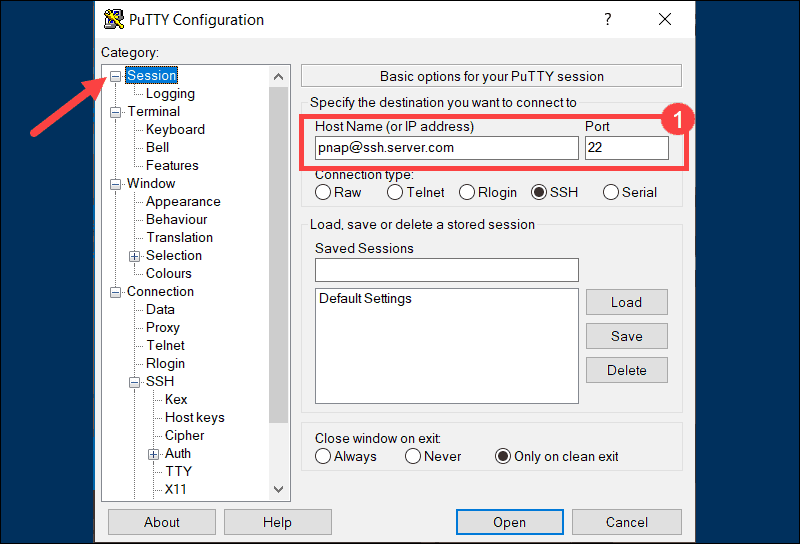
Connect to IoT Device via SSH
Once SSH is installed, connecting to an IoT device is straightforward:
- Ensure the IoT device is connected to the same network as your Mac.
- Obtain the IP address of the IoT device. This can usually be found in the device's settings or through the network router.
- Open Terminal and type the command
ssh username@IP_address, replacing "username" and "IP_address" with the appropriate values for your IoT device. - Enter the password when prompted to establish the connection.
With these steps, you can securely access and manage your IoT devices from your Mac.
Securing Your SSH Connection
While SSH provides a secure method for accessing IoT devices, additional measures can further enhance its security:
- Use Strong Passwords: Avoid using easily guessable passwords. Instead, opt for complex combinations of letters, numbers, and symbols.
- Enable Public Key Authentication: This method eliminates the need for passwords, reducing the risk of brute-force attacks.
- Disable Root Login: Restricting root access prevents unauthorized users from gaining administrative privileges.
- Change Default Port: Altering the default SSH port (22) can deter automated attacks targeting this port.
Implementing these best practices ensures that your SSH connections remain secure and resilient against potential threats.
Common SSH Errors and Troubleshooting
Even with proper setup, users may encounter issues when using SSH. Below are some common errors and their solutions:
- Error: Permission Denied (publickey): Ensure that the public key is correctly added to the authorized_keys file on the IoT device.
- Error: Connection Refused: Verify that the SSH service is running on the IoT device and that the correct IP address and port are being used.
- Error: Host Key Verification Failed: Delete the entry for the IoT device in the known_hosts file and reconnect.
By addressing these issues promptly, users can maintain seamless SSH connections to their IoT devices.
Best Practices for SSH Login in IoT
To maximize the security and efficiency of SSH login for IoT devices, consider the following best practices:
- Regularly Update Firmware: Keep IoT devices up to date with the latest security patches and firmware updates.
- Monitor Access Logs: Regularly review SSH access logs to detect any suspicious activity.
- Limit User Access: Restrict SSH access to only those users who require it, reducing the risk of unauthorized access.
Adhering to these practices ensures that your IoT devices remain secure and operational.
SSH Alternatives for IoT Devices
While SSH is the gold standard for secure remote access, there are alternative protocols that may suit specific IoT applications:
- Telnet: Although less secure, Telnet is still used in some legacy IoT systems due to its simplicity.
- TLS/SSL: Transport Layer Security (TLS) and Secure Sockets Layer (SSL) protocols can be used for securing data transmission in IoT environments.
- MQTT: Message Queuing Telemetry Transport (MQTT) is a lightweight protocol ideal for IoT devices with limited resources.
Evaluating these alternatives can help determine the most appropriate solution for your IoT setup.
Frequently Asked Questions
Here are some common questions about SSH login for IoT devices:
- Can SSH be used for all IoT devices? While SSH is widely supported, not all IoT devices have SSH capabilities. Check the device specifications for compatibility.
- Is SSH secure enough for sensitive data? When configured correctly, SSH provides robust security for transmitting sensitive data.
- How often should SSH keys be updated? It's recommended to update SSH keys periodically, especially in high-security environments.
These answers address key concerns and provide clarity on SSH usage in IoT setups.
Conclusion: Secure Your IoT Devices with SSH
SSH login for IoT devices is a powerful tool for ensuring secure remote access and management. By following the steps outlined in this guide, you can effectively download, install, and configure SSH on macOS, enhancing the security of your IoT devices.
We encourage you to implement the best practices discussed and regularly review your SSH configurations to stay ahead of potential threats. Your feedback and questions are valuable, so feel free to leave a comment or share this article with others who may find it useful. Together, we can create a safer and more secure IoT ecosystem.
For more information on SSH and IoT security, explore our other articles or consult reputable sources like the OpenSSH website and NIST cybersecurity guidelines.