In today's digital age, remote IoT device SSH tutorial is essential for anyone managing or monitoring internet-connected devices from afar. Whether you're a developer, network administrator, or hobbyist, understanding how to securely access and manage IoT devices via SSH (Secure Shell) is critical for ensuring device integrity and network security.
With the rapid growth of IoT devices globally, the ability to remotely access and configure these devices has become indispensable. The Internet of Things (IoT) market is projected to reach $1.5 trillion by 2030, according to Statista, highlighting the importance of secure remote management practices. This article will guide you through the step-by-step process of setting up and using SSH to manage your IoT devices remotely.
Our focus will be on providing a comprehensive guide to help you navigate the complexities of remote IoT device management. By the end of this tutorial, you'll have the knowledge and tools necessary to secure your IoT devices and ensure they function optimally, even when accessed from remote locations.
Read also:Free Remoteiot Display Chart Template Your Ultimate Guide To Data Visualization
Table of Contents
- Introduction to Remote IoT Device SSH
- What is SSH?
- Benefits of Using SSH for IoT Devices
- Setting Up SSH on IoT Devices
- Securing Your IoT Devices with SSH
- Essential Tools for Remote IoT Management
- Troubleshooting Common SSH Issues
- Best Practices for Remote IoT Device Management
- Automating SSH Connections
- Conclusion
Introduction to Remote IoT Device SSH
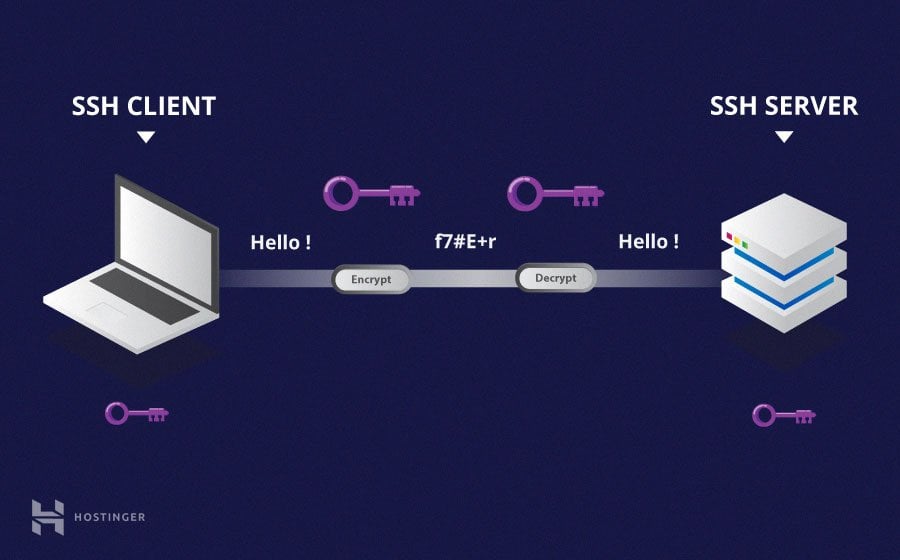
Remote IoT device SSH tutorial begins with understanding the basics of Secure Shell (SSH). SSH is a cryptographic network protocol used to securely connect to remote devices over an unsecured network. It ensures that all data exchanged between the client and server is encrypted, making it ideal for managing IoT devices remotely.
When working with IoT devices, the ability to remotely connect and manage them is crucial. SSH provides a secure channel for administrators to execute commands, transfer files, and monitor device performance. This section will cover the importance of SSH in IoT environments and why it should be a priority for anyone managing IoT devices.
What is SSH?
Definition and History
SSH, or Secure Shell, was first developed in 1995 by Tatu Ylönen to address the security vulnerabilities of earlier protocols like Telnet. Unlike Telnet, which transmits data in plaintext, SSH encrypts all communication, making it far more secure. Over the years, SSH has evolved into a standard protocol for secure remote access.
Key Features
- Encryption of data transmission
- Authentication mechanisms to verify user identity
- Support for various cryptographic algorithms
- Integration with other protocols for file transfer and tunneling
SSH is widely used across industries, from IT to manufacturing, to ensure secure communication between devices and servers. Its adaptability makes it a perfect fit for managing IoT devices remotely.
Benefits of Using SSH for IoT Devices
Using SSH for remote IoT device management offers several advantages:
- Enhanced Security: SSH encrypts all data exchanged between the client and server, protecting sensitive information from interception.
- Efficient Management: Administrators can easily execute commands, monitor performance, and troubleshoot issues without physically accessing the device.
- Scalability: SSH supports multiple connections, making it suitable for managing large fleets of IoT devices.
- Automation: SSH can be integrated with scripts and automation tools to streamline repetitive tasks.
These benefits make SSH an indispensable tool for anyone managing IoT devices in a professional or personal capacity.
Read also:How To Manage A Fleet Of Raspberry Pi For Free A Comprehensive Guide
Setting Up SSH on IoT Devices
Prerequisites
Before setting up SSH on your IoT device, ensure the following:
- The device has a stable internet connection.
- You have administrative access to the device.
- The device runs an operating system that supports SSH (e.g., Linux-based systems).
Installation Steps
Follow these steps to install and configure SSH on your IoT device:
- Log in to your IoT device via its local interface.
- Update the package list by running the command:
sudo apt update. - Install the SSH server by running:
sudo apt install openssh-server. - Start the SSH service using:
sudo systemctl start ssh. - Verify the service is running with:
sudo systemctl status ssh.
Once installed, you can connect to the device from a remote location using an SSH client.
Securing Your IoT Devices with SSH
Best Security Practices
While SSH is inherently secure, additional measures can enhance its protection:
- Use Strong Passwords: Avoid using default passwords and opt for complex, unique ones.
- Enable Public Key Authentication: This eliminates the need for passwords and adds an extra layer of security.
- Disable Root Login: Restrict direct access to the root account to prevent unauthorized access.
- Change the Default SSH Port: Moving away from the default port (22) can deter automated attacks.
- Use Firewall Rules: Limit SSH access to trusted IP addresses to reduce the risk of unauthorized access.
Implementing these practices will significantly improve the security of your IoT devices when accessed via SSH.
Essential Tools for Remote IoT Management
SSH Clients
Several SSH clients are available for different operating systems:
- Putty: A popular, free SSH client for Windows.
- OpenSSH: Pre-installed on most Linux and macOS systems.
- Termius: A cross-platform SSH client for mobile and desktop use.
Monitoring Tools
To effectively manage IoT devices remotely, consider using monitoring tools like:
- Prometheus: A powerful open-source monitoring system with alerting capabilities.
- Grafana: A visualization platform that works seamlessly with Prometheus.
- Zabbix: An enterprise-grade monitoring solution for large-scale environments.
These tools provide real-time insights into device performance and help identify potential issues before they escalate.
Troubleshooting Common SSH Issues
Connection Problems
If you encounter connection issues, consider the following:
- Check if the SSH service is running on the IoT device.
- Verify the IP address and port number are correct.
- Ensure there are no firewall rules blocking the connection.
Authentication Failures
Authentication issues can arise due to:
- Incorrect usernames or passwords.
- Public key mismatches.
- Disabled SSH access in the device's configuration.
Addressing these issues promptly will ensure uninterrupted access to your IoT devices.
Best Practices for Remote IoT Device Management
Adopting best practices for remote IoT device management is crucial for maintaining security and efficiency:
- Regularly Update Firmware: Keep your devices updated with the latest firmware to address security vulnerabilities.
- Implement Access Controls: Restrict access to only authorized personnel and devices.
- Monitor Device Activity: Regularly review logs to detect and respond to suspicious activities.
- Backup Configuration Files: Maintain backups of critical configuration files to facilitate quick recovery in case of issues.
Following these practices will help you maintain a secure and efficient IoT environment.
Automating SSH Connections
Using SSH Keys for Automation
Automating SSH connections can save time and reduce the risk of human error. Here's how to set it up:
- Generate an SSH key pair on your local machine:
ssh-keygen -t rsa. - Copy the public key to the IoT device:
ssh-copy-id user@iot-device. - Test the connection by logging in without a password.
Scripting SSH Commands
Use scripting languages like Python or Bash to automate repetitive SSH tasks. For example, you can write a script to execute a series of commands on multiple IoT devices simultaneously.
Conclusion
This remote IoT device SSH tutorial has provided a comprehensive guide to managing IoT devices securely and efficiently using SSH. From understanding the basics of SSH to implementing best practices for remote management, you now have the knowledge and tools necessary to safeguard your IoT devices.
We encourage you to apply these techniques in your own projects and share your experiences in the comments below. Don't forget to explore related articles on our site for more insights into IoT security and management. Together, let's build a safer, smarter IoT ecosystem!