In today's digital age, securely connecting remote IoT devices via P2P SSH on a Raspberry Pi with a free server has become an essential skill for tech enthusiasts, developers, and IT professionals. As more devices become interconnected, ensuring secure communication is paramount to protect sensitive data and maintain system integrity. This article will guide you through the process of setting up a secure connection using SSH on a Raspberry Pi while utilizing a free server for remote access.
With the proliferation of Internet of Things (IoT) devices, the need for secure communication channels has never been greater. Whether you're managing home automation systems, monitoring environmental sensors, or deploying industrial IoT solutions, secure connectivity is a fundamental requirement. This article will delve into the intricacies of establishing a secure connection using SSH, emphasizing the use of a Raspberry Pi as a cost-effective and versatile platform.
By the end of this article, you will have a comprehensive understanding of how to configure your Raspberry Pi for remote IoT P2P SSH access without the need for expensive cloud services. We will also explore best practices for securing your setup, ensuring that your IoT ecosystem remains robust and protected against potential threats.
Read also:Prmoviesemail Your Ultimate Guide To The Platform
Table of Contents
- Introduction to Secure IoT Connections
- Overview of Raspberry Pi as a Secure IoT Platform
- Understanding SSH for Secure Communication
- Implementing P2P SSH on Raspberry Pi
- Exploring Free Server Options for Remote Access
- Best Practices for Securing IoT Connections
- Data Protection and Encryption Techniques
- Common Issues and Troubleshooting
- Real-World Applications of Secure IoT Connections
- Conclusion and Call to Action
Introduction to Secure IoT Connections
As the world becomes increasingly interconnected, securing IoT devices has become a top priority. A secure connection ensures that sensitive data remains protected and that devices function reliably. In this section, we will explore the importance of secure IoT connections and the role that SSH plays in achieving this goal.
SSH (Secure Shell) is a cryptographic network protocol that facilitates secure communication over unsecured networks. By leveraging SSH, users can establish encrypted connections between devices, ensuring that data transmitted remains confidential and tamper-proof. For remote IoT deployments, SSH provides a robust solution for managing and monitoring devices from a distance.
The Raspberry Pi, with its affordability and versatility, serves as an ideal platform for implementing secure IoT solutions. Combining the power of SSH with the capabilities of a Raspberry Pi enables users to create a secure and efficient remote access system without breaking the bank.
Overview of Raspberry Pi as a Secure IoT Platform
The Raspberry Pi is a single-board computer that has gained immense popularity among hobbyists, educators, and professionals alike. Its compact size, low power consumption, and affordable price make it an attractive option for IoT projects. In this section, we will examine the features of the Raspberry Pi that make it suitable for secure IoT applications.
Key features of the Raspberry Pi include:
- Support for multiple operating systems, including Linux distributions optimized for IoT
- Built-in GPIO pins for interfacing with sensors and actuators
- Compatibility with a wide range of peripherals and expansion boards
- Community-driven support and extensive documentation
By leveraging the Raspberry Pi's capabilities, users can create custom solutions tailored to their specific IoT needs. Whether you're building a home automation system or deploying industrial-grade sensors, the Raspberry Pi provides a flexible and reliable foundation for secure IoT implementations.
Read also:Remoteiot Behind Router Example In Raspberry Pi A Comprehensive Guide
Understanding SSH for Secure Communication
SSH is a protocol designed to provide secure communication over unsecured networks. It encrypts data transmitted between devices, ensuring that sensitive information remains protected from unauthorized access. In this section, we will delve into the mechanics of SSH and its role in securing IoT connections.
Key benefits of using SSH for IoT include:
- Data encryption to prevent eavesdropping
- Authentication mechanisms to verify device identity
- Remote command execution capabilities
When implementing SSH for IoT, it is crucial to follow best practices to ensure maximum security. This includes using strong passwords, enabling public key authentication, and regularly updating software to address vulnerabilities.
Implementing P2P SSH on Raspberry Pi
Step 1: Initial Setup
Before configuring SSH, it is essential to set up your Raspberry Pi properly. This involves installing the operating system, updating software packages, and configuring network settings. Follow these steps to ensure a smooth setup process:
- Download the latest version of Raspberry Pi OS from the official website
- Write the image to an SD card using a tool like Etcher
- Insert the SD card into your Raspberry Pi and power it on
- Connect to your local network via Wi-Fi or Ethernet
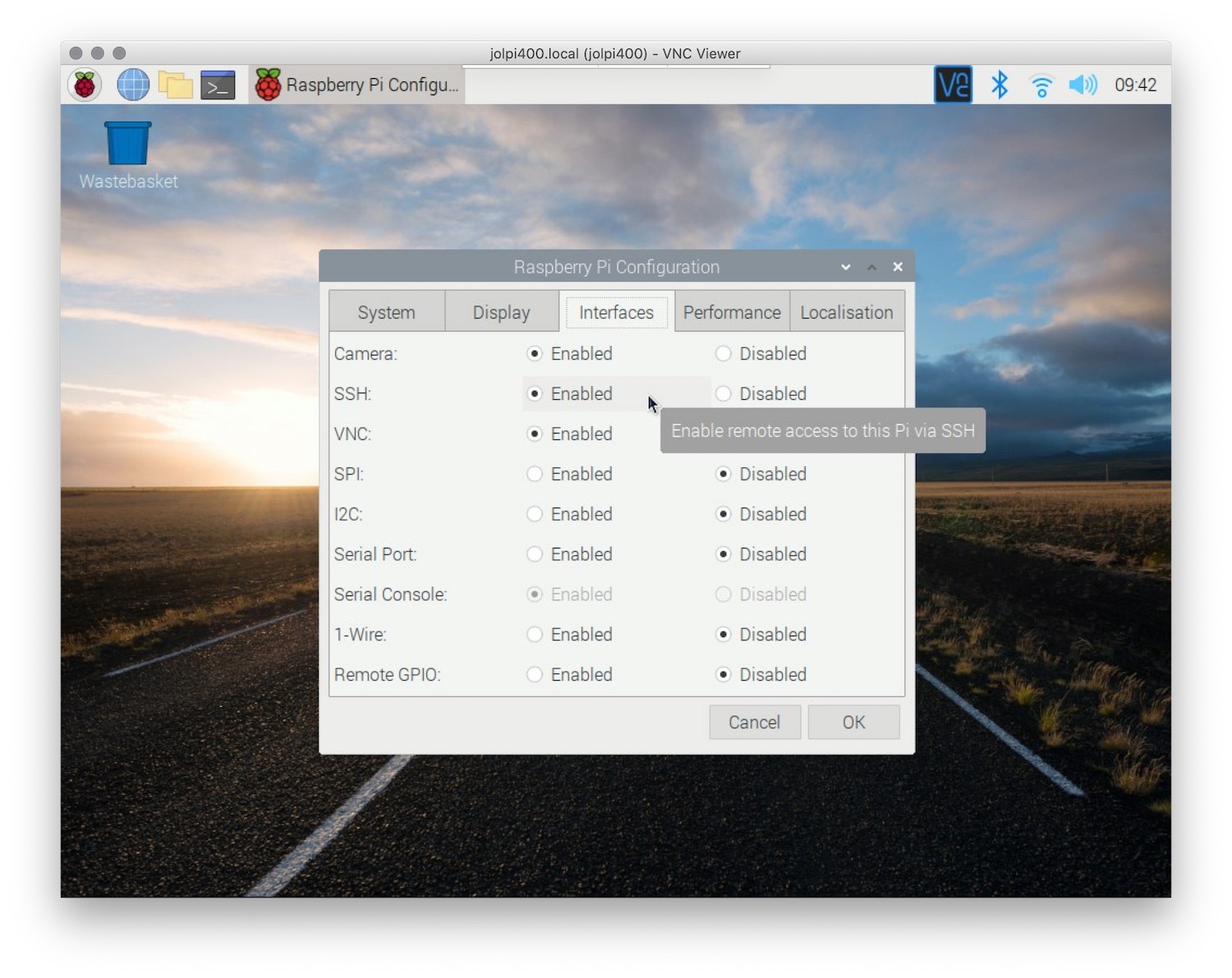
Step 2: Configuring SSH
Once your Raspberry Pi is set up, you can proceed to configure SSH. This involves enabling the SSH service and setting up authentication methods. Follow these steps to configure SSH on your Raspberry Pi:
- Enable SSH by navigating to the Raspberry Pi Configuration menu
- Generate SSH keys using the ssh-keygen command
- Copy the public key to the authorized_keys file
- Test the connection using an SSH client
Exploring Free Server Options for Remote Access
While cloud services offer convenient solutions for remote access, they often come with associated costs. Fortunately, there are free server options available that can be used to facilitate remote IoT P2P SSH connections. In this section, we will explore some of these options and their respective advantages.
Popular free server options include:
- ngrok: Provides secure tunnels for local servers
- LocalTunnel: Offers temporary public URLs for local servers
- ZeroTier: Enables virtual networking for remote devices
When selecting a free server option, consider factors such as ease of use, reliability, and security features. Each option has its strengths and weaknesses, so it is important to choose one that aligns with your specific requirements.
Best Practices for Securing IoT Connections
Securing IoT connections requires a multi-layered approach that addresses potential vulnerabilities at every level. In this section, we will discuss best practices for securing IoT connections, with a focus on SSH and Raspberry Pi configurations.
Key security best practices include:
- Using strong, unique passwords for all devices
- Enabling two-factor authentication (2FA) whenever possible
- Regularly updating firmware and software to address vulnerabilities
- Implementing firewalls and intrusion detection systems
By adhering to these best practices, you can significantly enhance the security of your IoT ecosystem and protect it from potential threats.
Data Protection and Encryption Techniques
Data protection is a critical component of secure IoT connections. In this section, we will explore encryption techniques and data protection strategies that can be employed to safeguard sensitive information.
Effective data protection strategies include:
- Using end-to-end encryption for data transmission
- Implementing secure storage solutions for sensitive data
- Regularly backing up important data to prevent loss
By combining encryption techniques with robust data protection measures, you can ensure that your IoT devices remain secure and your data remains confidential.
Common Issues and Troubleshooting
Despite best efforts, issues may arise when setting up secure IoT connections. In this section, we will address common problems encountered during the setup process and provide solutions to resolve them.
Common issues include:
- SSH connection failures due to incorrect configurations
- Network connectivity problems affecting remote access
- Security vulnerabilities resulting from outdated software
By identifying potential issues and implementing appropriate solutions, you can overcome challenges and ensure a smooth setup process.
Real-World Applications of Secure IoT Connections
Secure IoT connections have numerous real-world applications across various industries. In this section, we will explore some of these applications and their impact on modern technology.
Examples of real-world applications include:
- Smart home automation systems for enhanced convenience and security
- Industrial IoT solutions for monitoring and optimizing manufacturing processes
- Environmental monitoring systems for tracking climate change and natural disasters
By leveraging secure IoT connections, organizations can improve efficiency, reduce costs, and enhance overall performance.
Conclusion and Call to Action
In conclusion, securely connecting remote IoT devices via P2P SSH on a Raspberry Pi with a free server is a powerful solution for modern tech enthusiasts and professionals. By following the steps outlined in this article, you can create a secure and efficient remote access system tailored to your specific needs.
We encourage you to take action by experimenting with the techniques discussed in this article. Leave a comment below sharing your experiences or questions, and consider exploring other articles on our site for further insights into IoT and cybersecurity.