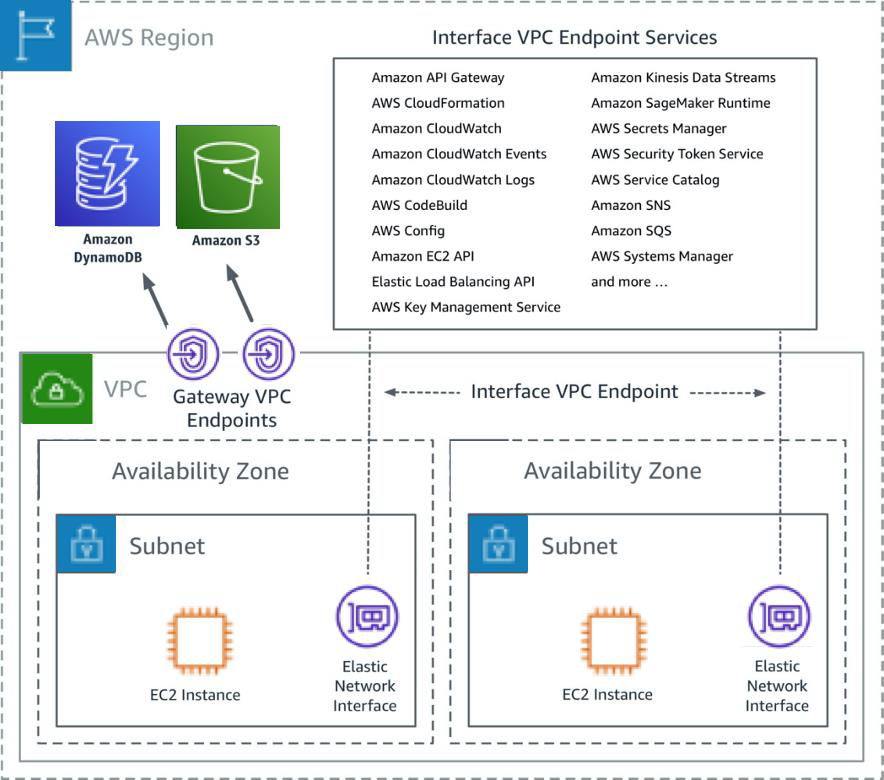
As the Internet of Things (IoT) continues to evolve, securely connecting remote IoT devices within a Virtual Private Cloud (VPC) on AWS has become a critical priority for businesses. The ability to manage and secure these connections ensures data integrity, compliance, and operational efficiency. This article will delve into the best practices and strategies for securely connecting remote IoT devices within an AWS VPC environment.
With the growing number of connected devices, the need for robust security measures has never been more important. Organizations must ensure that their IoT infrastructure is protected from unauthorized access and potential cyber threats. AWS provides a wide range of tools and services to help achieve this goal, but implementing them effectively requires a clear understanding of the ecosystem.
This guide will explore the key components of secure IoT connectivity, including network architecture, encryption methods, identity management, and monitoring tools. By the end of this article, you will have a comprehensive understanding of how to securely connect remote IoT devices within your VPC on AWS.
Read also:Vegamovies 29 Netflix Your Ultimate Guide To Streaming Entertainment
Table of Contents
- Introduction to Secure IoT Connectivity
- Understanding AWS VPC Basics
- IoT Security Challenges
- Building a Secure IoT Architecture
- Encryption Methods for IoT Devices
- Identity Management for IoT Devices
- Network Security Best Practices
- Monitoring Tools for IoT Security
- Case Studies: Real-World Implementations
- Conclusion and Next Steps
Introduction to Secure IoT Connectivity
Connecting remote IoT devices securely within an AWS VPC environment requires a well-planned strategy that addresses both technical and operational challenges. The first step is to understand the fundamentals of IoT connectivity and how it integrates with cloud infrastructure.
In this section, we will explore:
- The importance of secure IoT connectivity
- Key components of an AWS VPC
- How to align IoT security with business objectives
Secure connectivity is not just about protecting data; it also involves ensuring that devices operate efficiently and that system performance remains optimal. By leveraging AWS's advanced features, organizations can build a resilient and secure IoT ecosystem.
Understanding AWS VPC Basics
Before diving into the specifics of securely connecting IoT devices, it's essential to understand the basics of AWS VPC. A Virtual Private Cloud (VPC) is a logically isolated section of the AWS Cloud where you can launch AWS resources in a virtual network that you define.
Key Features of AWS VPC
AWS VPC offers several features that are crucial for secure IoT connectivity:
- IP Address Ranges: You can define your own IP address range, which allows for greater control over network segmentation.
- Subnets: Subnets enable you to divide your VPC into smaller segments, each with its own set of rules and policies.
- Security Groups: These act as virtual firewalls for your instances, controlling inbound and outbound traffic.
By properly configuring these components, you can create a secure environment for your IoT devices to operate within.
Read also:Securely Connect Remote Iot Vpc Raspberry Pi Free Download For Windows
IoT Security Challenges
Securing IoT devices presents unique challenges due to their diverse nature and the vast number of potential entry points for cyberattacks. Some of the key challenges include:
- Device Authentication: Ensuring that only authorized devices can connect to your network.
- Data Encryption: Protecting data both in transit and at rest.
- Network Segmentation: Isolating IoT devices from other parts of your network to minimize risk.
Addressing these challenges requires a multi-layered approach that combines strong authentication mechanisms, robust encryption protocols, and effective network segmentation strategies.
Building a Secure IoT Architecture
A secure IoT architecture is the foundation for protecting your devices and data. This section will outline the key components of such an architecture and how they can be implemented within an AWS VPC environment.
Network Segmentation
Network segmentation involves dividing your network into smaller, isolated segments. This reduces the attack surface and limits the potential impact of a security breach.
Device Authentication
Implementing strong authentication mechanisms is critical for ensuring that only authorized devices can access your network. AWS provides several tools, such as AWS IoT Core, to facilitate this process.
Data Encryption
Encrypting data both in transit and at rest is essential for maintaining data integrity and confidentiality. AWS offers a variety of encryption services, including AWS Key Management Service (KMS), to help secure your data.
Encryption Methods for IoT Devices
Encryption is a fundamental component of IoT security. By encrypting data, you can protect sensitive information from unauthorized access and ensure that it remains confidential.
- Transport Layer Security (TLS): TLS is widely used for securing communications between IoT devices and the cloud.
- Advanced Encryption Standard (AES): AES is a symmetric encryption algorithm commonly used for securing data at rest.
- Public Key Infrastructure (PKI): PKI provides a framework for managing digital certificates and public keys, enabling secure communication between devices.
Choosing the right encryption method depends on your specific use case and the capabilities of your devices.
Identity Management for IoT Devices
Identity management is critical for ensuring that only authorized devices and users can access your IoT network. AWS offers several services to help manage identities, including:
- AWS IoT Core: Provides device authentication and authorization capabilities.
- AWS Identity and Access Management (IAM): Allows you to manage user access to AWS resources.
- Cognito: Enables user authentication and synchronization across devices.
By implementing these tools, you can create a secure and scalable identity management system for your IoT devices.
Network Security Best Practices
Network security is a critical component of any IoT deployment. By following best practices, you can minimize the risk of cyberattacks and ensure the integrity of your network.
Firewall Rules
Configuring firewall rules is essential for controlling inbound and outbound traffic. AWS Security Groups and Network Access Control Lists (NACLs) provide powerful tools for managing these rules.
Intrusion Detection
Implementing intrusion detection systems (IDS) can help identify and respond to potential threats in real time. AWS GuardDuty is a managed threat detection service that continuously monitors for malicious activity and unauthorized behavior.
Regular Audits
Conducting regular security audits ensures that your network remains compliant with industry standards and best practices. AWS Config and AWS Trusted Advisor provide tools for monitoring and assessing your infrastructure.
Monitoring Tools for IoT Security
Monitoring your IoT network is essential for detecting and responding to security incidents. AWS offers several tools to help you monitor your infrastructure, including:
- AWS CloudWatch: Provides real-time monitoring of metrics and logs.
- AWS Shield: Protects your applications from Distributed Denial of Service (DDoS) attacks.
- AWS WAF: Web Application Firewall that helps protect your web applications from common web exploits.
By leveraging these tools, you can gain visibility into your IoT environment and respond quickly to potential threats.
Case Studies: Real-World Implementations
Real-world case studies provide valuable insights into how organizations have successfully implemented secure IoT solutions. Here are a few examples:
Case Study 1: Smart City Initiative
A major city implemented a smart city initiative using AWS IoT Core to securely connect thousands of IoT devices. By leveraging AWS VPC and encryption services, they were able to ensure the security and reliability of their network.
Case Study 2: Industrial Automation
An industrial automation company used AWS to build a secure IoT architecture for managing their manufacturing processes. By implementing strong authentication and encryption protocols, they minimized the risk of cyberattacks and ensured operational efficiency.
Case Study 3: Healthcare Monitoring
A healthcare provider deployed IoT devices to monitor patient health in real time. By using AWS services for identity management and network security, they ensured the privacy and security of patient data.
Conclusion and Next Steps
Securing remote IoT devices within an AWS VPC environment requires a comprehensive approach that addresses both technical and operational challenges. By following the best practices outlined in this article, you can build a secure and resilient IoT infrastructure that meets your business needs.
To take the next steps:
- Review your current IoT architecture and identify areas for improvement.
- Implement AWS services for identity management, encryption, and network security.
- Monitor your infrastructure regularly to ensure compliance and detect potential threats.
We encourage you to share your thoughts and experiences in the comments section below. Additionally, feel free to explore other articles on our site for more insights into IoT security and AWS best practices.