In today's interconnected world, securely connect remote IoT P2P SSH Raspberry Pi free has become a necessity for tech enthusiasts, hobbyists, and professionals alike. The rise of IoT devices and remote work has increased the demand for secure communication channels. Understanding how to establish a secure connection without breaking the bank is crucial for anyone working with Raspberry Pi.
As more people adopt IoT devices, the need for secure remote access grows exponentially. Whether you're a beginner or an advanced user, setting up a secure SSH connection for your Raspberry Pi can protect your data and privacy. This guide will walk you through the process step by step, ensuring your IoT devices remain safe and accessible.
By the end of this article, you'll have a comprehensive understanding of how to securely connect your Raspberry Pi remotely using peer-to-peer (P2P) SSH, all while keeping costs low. Let's dive in!
Read also:How To Manage A Fleet Of Raspberry Pi For Free A Comprehensive Guide
Table of Contents
- Introduction to Secure IoT Connections
- Raspberry Pi Overview
- Understanding SSH Basics
- Remote Access Methods for IoT Devices
- Peer-to-Peer SSH Explained
- Step-by-Step Setup Guide
- Security Best Practices
- Cost-Effective Solutions
- Common Issues and Troubleshooting
- Conclusion and Next Steps
Introduction to Secure IoT Connections
As the Internet of Things (IoT) continues to expand, so does the need for secure remote connections. IoT devices often require remote access for monitoring, maintenance, and updates. However, ensuring that these connections are secure is paramount to protecting sensitive data and preventing unauthorized access.
Securely connecting remote IoT devices using SSH (Secure Shell) is one of the most reliable methods available. SSH provides encrypted communication between devices, making it an ideal choice for securing IoT connections. By leveraging peer-to-peer (P2P) SSH, you can establish a direct connection without relying on third-party services, reducing potential security risks.
Why Use Raspberry Pi for IoT Projects?
Raspberry Pi has become a popular choice for IoT projects due to its affordability, versatility, and ease of use. With its compact size and powerful capabilities, Raspberry Pi serves as an excellent platform for experimenting with IoT applications. Additionally, its open-source nature allows users to customize and optimize their setups for specific needs.
Raspberry Pi Overview
Raspberry Pi is a series of small single-board computers developed by the Raspberry Pi Foundation. Originally designed for educational purposes, it has since gained widespread adoption among hobbyists, developers, and professionals. The Raspberry Pi's affordability and flexibility make it an ideal choice for IoT projects.
Key features of Raspberry Pi include:
- Compact size
- Low power consumption
- Multiple GPIO pins for interfacing with sensors and actuators
- Support for various operating systems, including Linux distributions
Choosing the Right Raspberry Pi Model
When selecting a Raspberry Pi for your IoT project, consider the following factors:
Read also:Mkvmoviespoint Ink Your Ultimate Destination For Movie Downloads
- Processing power
- Memory capacity
- Connectivity options (Wi-Fi, Bluetooth, Ethernet)
- Power supply requirements
For most IoT applications, the Raspberry Pi 4 Model B is a popular choice due to its balanced performance and connectivity options.
Understanding SSH Basics
SSH (Secure Shell) is a cryptographic network protocol used for secure communication over an unsecured network. It provides a secure channel for remote access to devices, making it an essential tool for managing IoT setups.
Key features of SSH include:
- Encryption of data in transit
- Authentication mechanisms (passwords, public key authentication)
- Support for tunneling and port forwarding
How SSH Works
SSH works by establishing a secure connection between a client and a server. The client initiates the connection, and the server authenticates the client using either a password or a public key. Once authenticated, the client and server exchange encrypted data, ensuring privacy and integrity.
Remote Access Methods for IoT Devices
There are several methods for remotely accessing IoT devices, each with its own advantages and disadvantages. Below are some of the most common methods:
- SSH
- VPN
- Cloud-based services
- Peer-to-peer (P2P) connections
Advantages of P2P SSH
Peer-to-peer (P2P) SSH offers several advantages over other remote access methods:
- No reliance on third-party services
- Reduced latency
- Enhanced security through direct connections
Peer-to-Peer SSH Explained
Peer-to-peer (P2P) SSH allows two devices to connect directly without the need for an intermediary server. This method offers several benefits, including improved security and reduced latency. By eliminating the need for a third-party service, P2P SSH minimizes potential security risks.
Setting Up P2P SSH
To set up P2P SSH, you'll need to configure both the client and server devices. Below are the basic steps:
- Install SSH on both devices
- Generate and exchange public keys
- Configure firewall settings to allow SSH traffic
- Test the connection to ensure it works
Step-by-Step Setup Guide
Follow this step-by-step guide to securely connect your Raspberry Pi remotely using P2P SSH:
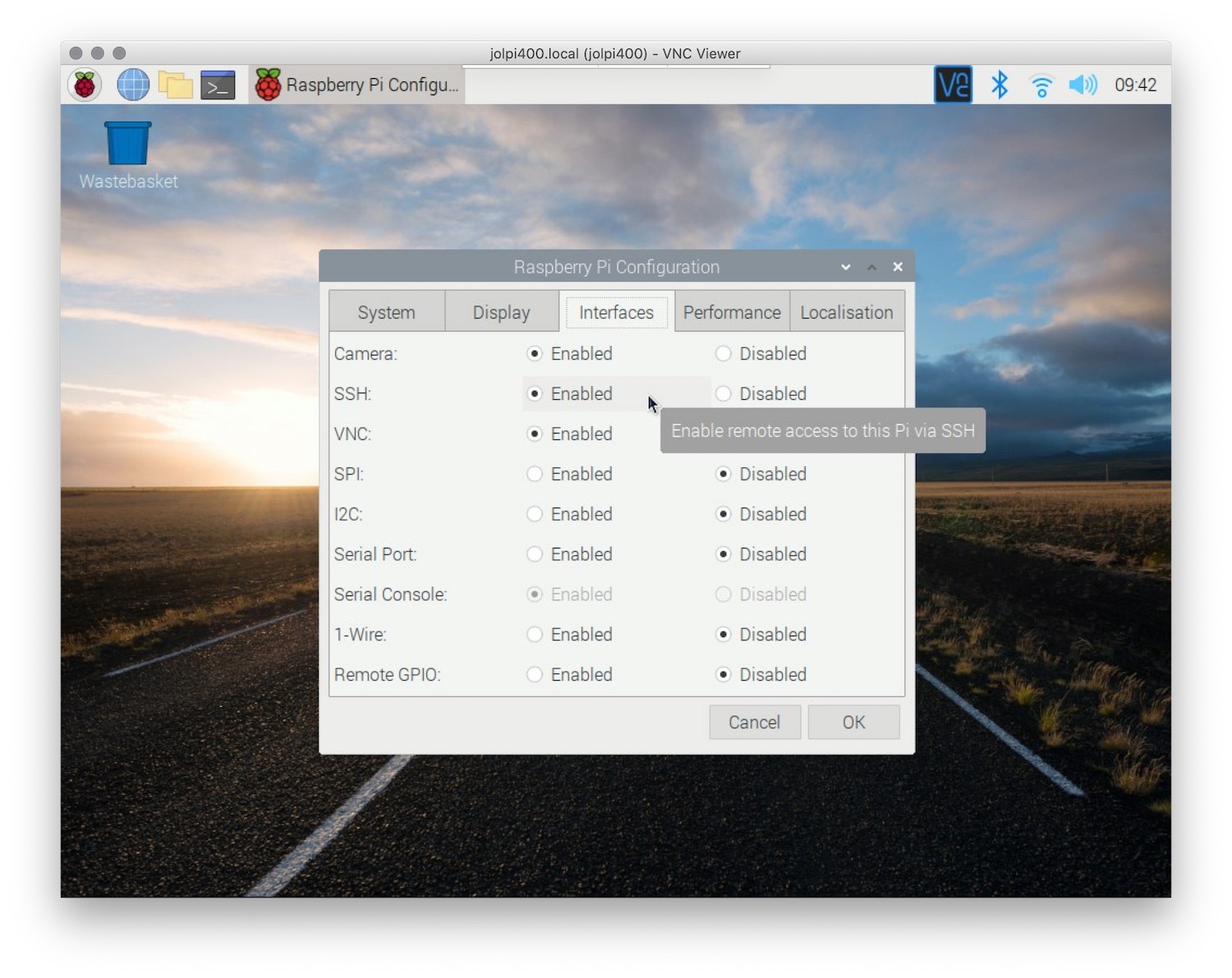
Step 1: Install SSH on Raspberry Pi
To install SSH on your Raspberry Pi, follow these steps:
- Open the terminal on your Raspberry Pi
- Run the command:
sudo apt update - Run the command:
sudo apt install openssh-server - Verify SSH is running with:
sudo systemctl status ssh
Step 2: Generate Public Key
Generate a public key on your client device:
- Open the terminal
- Run the command:
ssh-keygen -t rsa -b 4096 - Follow the prompts to save the key
Step 3: Exchange Public Keys
Exchange public keys between the client and server devices:
- COPY the public key from the client device
- PASTE it into the
~/.ssh/authorized_keysfile on the Raspberry Pi
Security Best Practices
Implementing security best practices is crucial when setting up remote IoT connections. Below are some tips to enhance the security of your SSH setup:
- Use strong, unique passwords
- Enable public key authentication
- Disable password authentication
- Change the default SSH port
- Regularly update your Raspberry Pi's operating system
Cost-Effective Solutions
One of the biggest advantages of using Raspberry Pi for IoT projects is its affordability. By leveraging open-source software and free tools, you can set up a secure remote connection without incurring significant costs. Below are some cost-effective solutions:
- Use free SSH clients like PuTTY or OpenSSH
- Utilize open-source operating systems like Raspbian
- Implement free security tools like Fail2Ban
Common Issues and Troubleshooting
Even with careful planning, issues can arise when setting up remote IoT connections. Below are some common problems and their solutions:
- Issue: SSH connection fails
Solution: Check firewall settings and ensure SSH is enabled - Issue: Public key authentication fails
Solution: Verify the public key is correctly added to the authorized_keys file - Issue: High latency
Solution: Optimize network settings and consider using P2P SSH
Conclusion and Next Steps
In conclusion, securely connecting remote IoT devices using P2P SSH on a Raspberry Pi is an effective and cost-efficient solution. By following the steps outlined in this guide, you can establish a secure connection that protects your data and privacy. Remember to implement security best practices and regularly update your systems to stay protected.
We encourage you to share your thoughts and experiences in the comments section below. Have you tried setting up a P2P SSH connection for your Raspberry Pi? What challenges did you face, and how did you overcome them? Additionally, feel free to explore other articles on our site for more tips and tutorials on IoT and Raspberry Pi projects.