RemoteIoT SSH AWS Example is a critical topic for those looking to secure and manage IoT devices remotely using AWS infrastructure. As IoT technology continues to evolve, understanding how to establish secure connections through SSH (Secure Shell) on AWS becomes essential for developers, engineers, and IT professionals. This guide will provide a detailed overview of the process, ensuring you gain the necessary expertise to implement it effectively.
In today's digital age, the Internet of Things (IoT) plays a pivotal role in various industries, from healthcare to manufacturing. With IoT devices becoming more widespread, securing these devices remotely is paramount. AWS offers robust solutions for managing IoT devices, and SSH serves as a secure communication protocol to access these devices.
This article will explore the RemoteIoT SSH AWS example in-depth, covering everything from setting up the infrastructure to best practices for maintaining security. Whether you're a beginner or an experienced professional, this guide aims to equip you with the knowledge and tools needed to implement secure IoT solutions.
Read also:Free Download Remoteiot Vpc Your Ultimate Guide To Remote Access
Table of Contents
- Introduction to RemoteIoT SSH AWS Example
- What is RemoteIoT SSH?
- Setting Up SSH on AWS
- Connecting IoT Devices via SSH
- Enhancing Security with SSH
- Tools and Technologies
- Best Practices for RemoteIoT SSH
- Troubleshooting Common Issues
- Real-World Examples
- Conclusion
Introduction to RemoteIoT SSH AWS Example
Understanding the RemoteIoT SSH AWS example begins with recognizing the significance of IoT devices and their role in modern technology. IoT devices are connected to the internet, enabling them to collect and exchange data. However, ensuring secure access to these devices is crucial, especially when managing them remotely.
AWS provides a scalable and secure infrastructure for IoT applications. By leveraging SSH, users can establish encrypted connections to IoT devices hosted on AWS, ensuring data integrity and confidentiality. This section will delve into the basics of SSH and its integration with AWS for IoT applications.
What is RemoteIoT SSH?
Defining SSH
SSH, or Secure Shell, is a cryptographic network protocol designed for secure communication over unsecured networks. It provides a secure channel for remote login and command execution, making it an ideal choice for managing IoT devices.
Integration with IoT
When combined with IoT, SSH allows users to access and manage IoT devices remotely. This integration is particularly useful in scenarios where physical access to devices is not feasible. AWS further enhances this capability by offering a robust infrastructure for hosting and managing IoT applications.
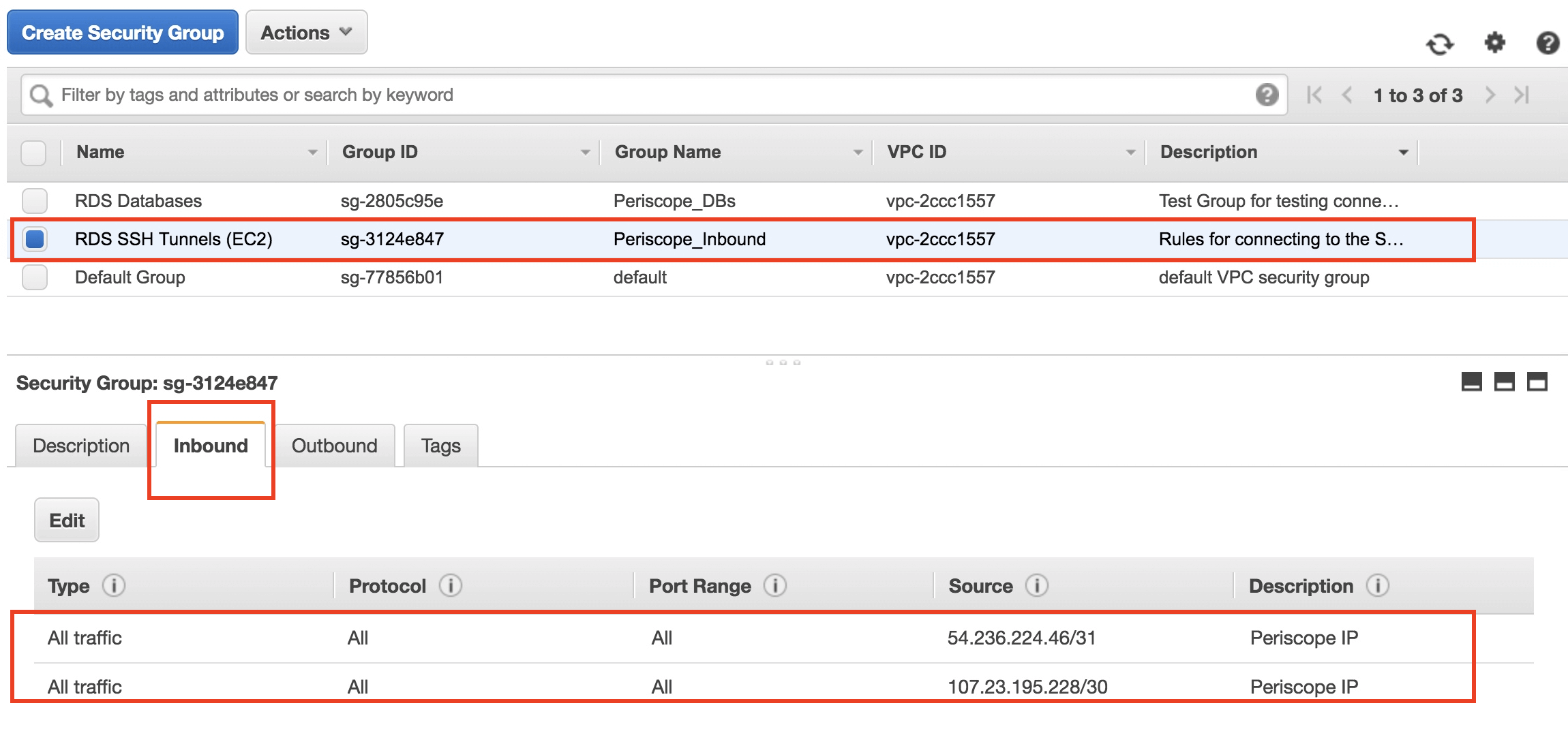
Setting Up SSH on AWS
Setting up SSH on AWS involves several steps, including creating an EC2 instance, generating SSH keys, and configuring security groups. Below is a step-by-step guide:
Read also:Erome Punjabi A Rising Star In The World Of Entertainment
- Create an EC2 instance: Launch an EC2 instance on AWS and select the appropriate AMI (Amazon Machine Image).
- Generate SSH keys: Use the AWS Management Console to generate SSH key pairs for secure access.
- Configure security groups: Set up security groups to allow SSH traffic on port 22.
Connecting IoT Devices via SSH
Prerequisites
Before connecting IoT devices via SSH, ensure the following prerequisites are met:
- The IoT device is connected to the internet.
- The device has SSH server software installed and running.
- Security credentials, such as SSH keys, are properly configured.
Steps to Connect
To connect IoT devices via SSH, follow these steps:
- Log in to your AWS Management Console.
- Access the EC2 instance hosting the IoT device.
- Use an SSH client to connect to the device using the generated SSH key.
Enhancing Security with SSH
Security is a top priority when managing IoT devices remotely. Here are some best practices to enhance security with SSH:
- Use strong, unique SSH keys and avoid sharing them across multiple devices.
- Disable password-based authentication and rely solely on key-based authentication.
- Regularly update and patch SSH server software to protect against vulnerabilities.
Tools and Technologies
SSH Clients
Several SSH clients are available for different operating systems. Popular options include:
- OpenSSH: A widely-used open-source SSH client for Linux and macOS.
- PuTTY: A free SSH client for Windows users.
Monitoring Tools
To ensure the security and performance of your IoT devices, consider using monitoring tools such as:
- AWS CloudWatch: Provides real-time monitoring of AWS resources and applications.
- Logstash: A server-side data processing pipeline for collecting and analyzing logs.
Best Practices for RemoteIoT SSH
Implementing best practices is essential for maintaining secure and efficient IoT deployments. Below are some recommendations:
- Limit SSH access to trusted IP addresses using security groups.
- Regularly audit SSH logs to detect and respond to unauthorized access attempts.
- Use multi-factor authentication (MFA) for an additional layer of security.
Troubleshooting Common Issues
Connection Problems
If you encounter connection issues while accessing IoT devices via SSH, consider the following solutions:
- Verify that the security group allows SSH traffic on port 22.
- Ensure the SSH server is running on the IoT device.
Performance Issues
To address performance issues, consider the following:
- Optimize SSH configurations for better performance.
- Use compression to reduce data transfer overhead.
Real-World Examples
Several organizations have successfully implemented RemoteIoT SSH AWS solutions. For instance, a manufacturing company used SSH to remotely monitor and manage IoT sensors in their production facilities. By leveraging AWS infrastructure, they ensured secure and reliable access to critical data.
Conclusion
RemoteIoT SSH AWS example demonstrates the power of combining IoT technology with secure communication protocols. By following the steps outlined in this guide, you can effectively manage and secure IoT devices remotely. Remember to adhere to best practices and continuously monitor your systems for potential threats.
We encourage readers to share their experiences and insights in the comments section below. Additionally, explore other articles on our website for more information on IoT and AWS solutions. Together, let's build a safer and more connected digital world.