As the Internet of Things (IoT) continues to expand, remote management of IoT devices has become a critical need for businesses and individuals alike. However, accessing these devices behind a firewall can be challenging, especially when security protocols are in place. Fortunately, using a Mac server as an intermediary can simplify the process while maintaining security. In this article, we'll explore how to use remote IoT behind a firewall using a Mac server example.
Remote IoT management offers numerous advantages, including improved efficiency, reduced downtime, and enhanced monitoring capabilities. However, navigating firewalls and network restrictions can complicate the setup. Understanding the correct configuration and best practices is essential to ensure seamless connectivity.
This guide will provide step-by-step instructions, practical examples, and expert tips to help you successfully deploy and manage IoT devices behind firewalls using a Mac server. By the end of this article, you'll have the knowledge and tools to implement a secure and efficient solution for your IoT infrastructure.
Read also:Aag Maal The Ultimate Guide To Understanding Its Importance Applications And Benefits
Table of Contents:
- Introduction to Remote IoT
- Understanding Firewall Challenges
- Why Use a Mac Server?
- Setting Up the Mac Server
- Configuring IoT Devices
- Securing Your Connection
- Troubleshooting Common Issues
- Best Practices for Remote IoT
- Case Study: Mac Server Example
- Conclusion and Next Steps
Introduction to Remote IoT
Remote IoT refers to the ability to monitor, manage, and control Internet of Things devices from a distant location. This capability is particularly valuable for industries such as manufacturing, agriculture, healthcare, and smart homes, where real-time data access and device management are essential. However, remote IoT deployment often encounters challenges, especially when devices are located behind firewalls or within restricted networks.
Why Is Remote IoT Important?
Remote IoT allows organizations to:
- Reduce operational costs by minimizing on-site visits.
- Improve device uptime through proactive monitoring and maintenance.
- Enhance data collection and analysis for better decision-making.
- Ensure compliance with industry standards and security protocols.
Key Benefits of Remote IoT
By leveraging remote IoT, businesses can achieve:
- Increased scalability and flexibility in managing IoT devices.
- Improved security through centralized control and monitoring.
- Enhanced efficiency by automating routine tasks and alerts.
Understanding Firewall Challenges
Firewalls are designed to protect networks from unauthorized access, but they can also create barriers for remote IoT connectivity. Firewalls typically block incoming traffic unless specific rules are configured to allow it. This creates challenges for IoT devices that need to communicate with external systems.
Common Firewall Issues
- Port restrictions: Many firewalls block specific ports required for IoT communication.
- IP whitelisting: Some networks only allow connections from predefined IP addresses.
- Encryption requirements: Firewalls may enforce encryption protocols that IoT devices are not equipped to handle.
Solutions to Firewall Challenges
To overcome these challenges, organizations can:
Read also:Hdhub4u South Indian Hindi Dubbed Your Ultimate Guide To Mustwatch Movies
- Use secure tunneling protocols like SSH or TLS.
- Implement dynamic DNS for easier access.
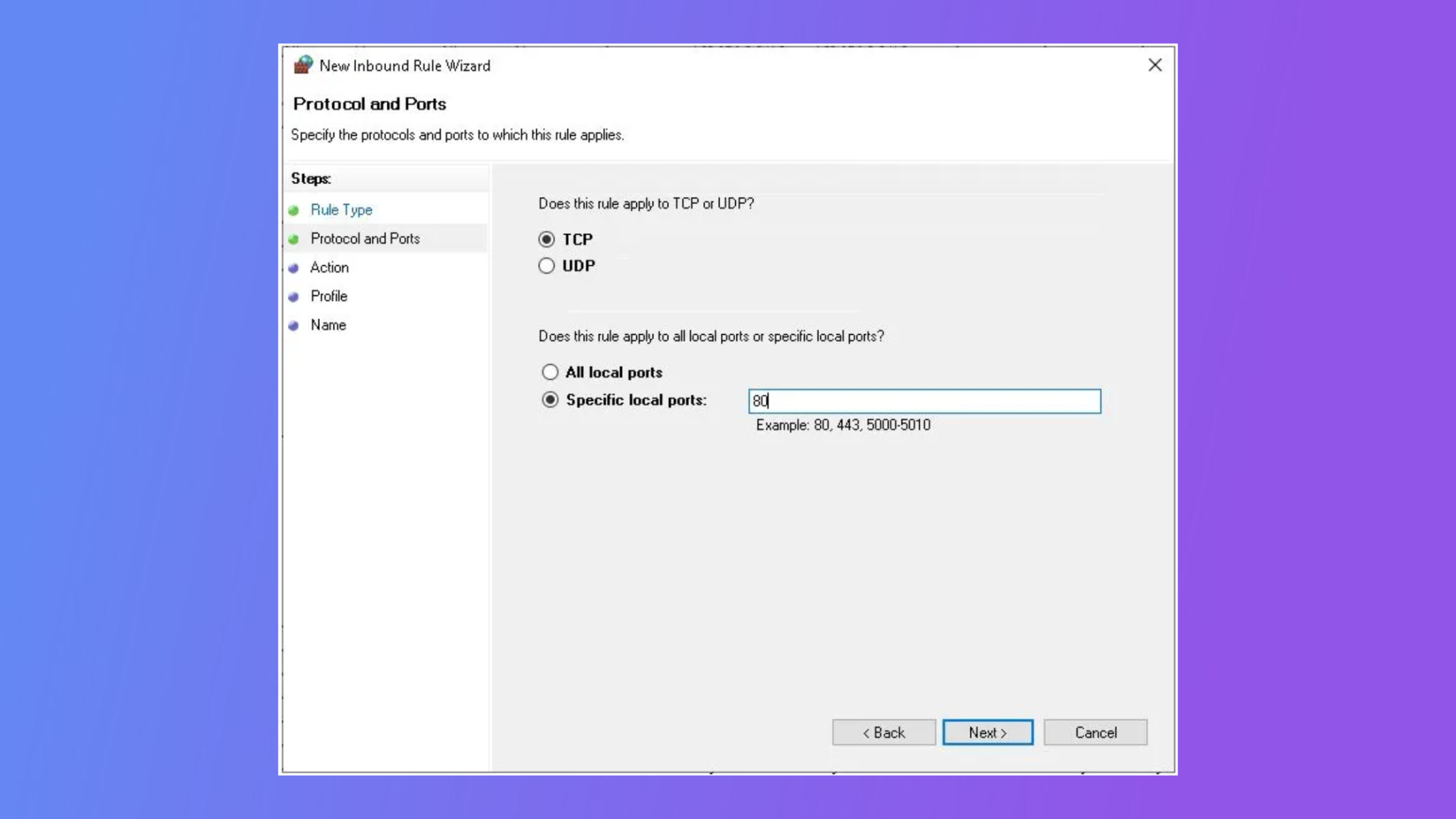
- Configure port forwarding rules on the firewall.
Why Use a Mac Server?
A Mac server provides a robust and user-friendly platform for managing remote IoT devices. With its built-in support for secure communication protocols and ease of use, a Mac server can act as a bridge between IoT devices and external networks. Additionally, macOS offers advanced features like file sharing, remote access, and automation tools that simplify IoT management.
Advantages of Using a Mac Server
- Seamless integration with macOS and iOS devices.
- Strong security features, including encryption and authentication.
- Easy-to-use interface for non-technical users.
Setting Up the Mac Server
Setting up a Mac server for remote IoT involves several steps, including hardware preparation, software installation, and network configuration. Below is a detailed guide to help you through the process.
Hardware Requirements
- A Mac computer with sufficient storage and processing power.
- A stable internet connection with a static IP address or dynamic DNS.
- A firewall or router that supports port forwarding.
Software Installation
To set up the Mac server:
- Install macOS Server from the App Store.
- Configure server settings, including hostname and administrator credentials.
- Enable required services such as File Sharing, Remote Access, and Web.
Configuring IoT Devices
Once the Mac server is set up, the next step is to configure the IoT devices to communicate with the server. This involves setting up device profiles, network settings, and security protocols.
Device Configuration Steps
- Connect the IoT devices to the local network.
- Assign static IP addresses to ensure consistent connectivity.
- Configure device settings to use the Mac server as a gateway.
Security Considerations
- Enable encryption for all device communications.
- Use strong passwords and multi-factor authentication.
- Regularly update firmware to protect against vulnerabilities.
Securing Your Connection
Security is paramount when managing IoT devices remotely. By implementing robust security measures, you can protect your network and devices from unauthorized access.
Best Security Practices
- Use secure tunneling protocols such as SSH or TLS.
- Implement firewalls and intrusion detection systems.
- Regularly monitor network activity for suspicious behavior.
Encryption Protocols
Some recommended encryption protocols include:
- SSL/TLS for secure web connections.
- IPSec for secure network tunnels.
- SSH for secure remote access.
Troubleshooting Common Issues
Despite careful planning, issues may arise during the setup and operation of remote IoT systems. Below are some common problems and their solutions.
Connection Problems
- Check network settings and ensure proper configuration.
- Verify firewall rules and port forwarding settings.
- Test connectivity using tools like ping and traceroute.
Performance Issues
- Optimize server settings for better performance.
- Limit the number of simultaneous connections.
- Use caching and compression techniques to reduce bandwidth usage.
Best Practices for Remote IoT
To ensure successful deployment and operation of remote IoT systems, it's essential to follow best practices. These practices encompass security, scalability, and maintenance aspects.
Security Best Practices
- Regularly update server and device software.
- Implement strict access controls and permissions.
- Conduct regular security audits and assessments.
Scalability Best Practices
- Plan for future growth and expansion.
- Use modular architecture for easy upgrades.
- Monitor system performance and adjust resources as needed.
Case Study: Mac Server Example
Let's consider a real-world example of using a Mac server for remote IoT management. A small business wants to monitor temperature and humidity levels in its warehouse using IoT sensors. By setting up a Mac server as an intermediary, the business can access sensor data remotely while maintaining security.
Implementation Steps
- Install macOS Server on a dedicated Mac computer.
- Configure network settings to allow sensor communication.
- Set up a secure web interface for remote access.
Results and Benefits
After implementation, the business enjoys:
- Real-time monitoring of warehouse conditions.
- Improved inventory management through automated alerts.
- Enhanced security with encrypted connections.
Conclusion and Next Steps
In conclusion, managing remote IoT devices behind a firewall using a Mac server is a practical and secure solution for businesses and individuals. By following the steps outlined in this guide, you can successfully deploy and maintain a robust IoT infrastructure.
To take the next step, consider:
- Implementing the setup in your own environment.
- Exploring additional features and services offered by macOS Server.
- Sharing your experience and feedback with the community.
We invite you to leave a comment below, share this article with your network, or explore other related articles on our site. Together, we can build a safer and more connected IoT ecosystem.
References: