In the rapidly evolving world of the Internet of Things (IoT), managing devices and ensuring secure connections has become a critical challenge for organizations. IoT management platforms play a pivotal role in addressing these challenges, and incorporating free SSH keys is a powerful way to enhance security and reduce costs. This article delves into the intricacies of IoT management platforms that offer free SSH keys, exploring their benefits, implementation strategies, and best practices.
As IoT adoption continues to grow exponentially, the demand for robust and secure management solutions has surged. With billions of connected devices operating globally, the importance of secure authentication mechanisms like SSH keys cannot be overstated. These keys provide an encrypted method of accessing devices, ensuring data integrity and protecting against unauthorized access.
This comprehensive guide aims to provide actionable insights into leveraging free SSH keys within IoT management platforms. Whether you're a tech enthusiast, a business owner, or an IT professional, this article will equip you with the knowledge and tools needed to make informed decisions about securing your IoT ecosystem.
Read also:How To Manage A Fleet Of Raspberry Pi For Free A Comprehensive Guide
Table of Contents
- Introduction to IoT Management Platforms
- Understanding SSH and Its Role in IoT
- Why Use Free SSH Keys in IoT?
- Top IoT Management Platforms Offering Free SSH Keys
- Steps to Implement Free SSH Keys
- Enhancing Security with SSH Keys
- Best Practices for Managing SSH Keys
- Scalability Considerations for IoT Systems
- Cost Implications of Using Free SSH Keys
- The Future of IoT Management Platforms
- Conclusion and Next Steps
Introduction to IoT Management Platforms
IoT management platforms are designed to streamline the deployment, monitoring, and management of IoT devices. These platforms offer a centralized interface for managing large-scale IoT ecosystems, ensuring efficient operations and secure communications. With the integration of free SSH keys, these platforms provide an additional layer of security, making them indispensable for modern businesses.
IoT management platforms that offer free SSH keys cater to organizations looking to optimize costs without compromising on security. These platforms often include features such as device provisioning, remote monitoring, and firmware updates, all secured by robust authentication mechanisms like SSH.
For organizations new to IoT, understanding the capabilities of these platforms is crucial. They not only simplify device management but also enhance data security, ensuring compliance with industry standards and regulations.
Understanding SSH and Its Role in IoT
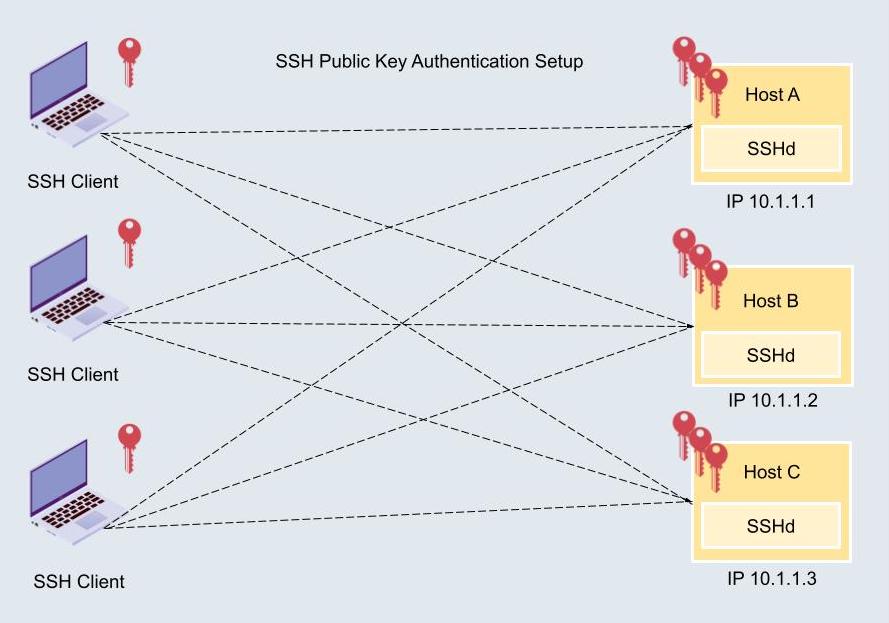
Secure Shell (SSH) is a cryptographic protocol used to secure communications over an unsecured network. In the context of IoT, SSH plays a vital role in securing device connections and data transmissions. By using SSH keys, organizations can authenticate devices and users without relying on passwords, reducing the risk of unauthorized access.
How SSH Works in IoT
SSH operates by establishing an encrypted connection between a client and a server. In IoT, this means securing communications between IoT devices and the management platform. Here's how it works:
- Key Generation: A pair of cryptographic keys (public and private) is generated for each device.
- Authentication: The public key is shared with the server, while the private key remains with the device.
- Encryption: All communications between the device and the server are encrypted using these keys.
This process ensures that even if data is intercepted, it cannot be deciphered without the private key.
Read also:Erome Your Ultimate Guide To Understanding And Exploring
Why Use Free SSH Keys in IoT?
Using free SSH keys in IoT management platforms offers several advantages. Firstly, it eliminates the need for purchasing expensive licensing solutions, making it an attractive option for small and medium-sized enterprises. Secondly, free SSH keys provide the same level of security as paid alternatives, ensuring robust protection against cyber threats.
Benefits of Free SSH Keys
- Cost Efficiency: Reduces operational expenses by eliminating licensing fees.
- Enhanced Security: Provides strong encryption and authentication mechanisms.
- Scalability: Easily scalable to accommodate growing IoT ecosystems.
- Ease of Use: Simple to implement and manage, even for non-technical users.
Organizations leveraging free SSH keys can focus their resources on innovation and growth rather than security infrastructure.
Top IoT Management Platforms Offering Free SSH Keys
Several IoT management platforms offer free SSH keys as part of their feature set. These platforms are designed to cater to a wide range of industries and use cases, ensuring flexibility and adaptability. Below are some of the top platforms in this category:
Platform 1: Platform A
Platform A is renowned for its user-friendly interface and robust security features. It offers free SSH keys as part of its standard package, making it an ideal choice for organizations seeking cost-effective solutions.
Platform 2: Platform B
Platform B focuses on scalability, allowing organizations to manage thousands of devices effortlessly. Its free SSH key integration ensures secure communications across all devices in the network.
Platform 3: Platform C
Platform C is tailored for enterprises requiring advanced analytics and reporting capabilities. Its free SSH key feature enhances security while providing insights into device performance and network health.
Steps to Implement Free SSH Keys
Implementing free SSH keys in an IoT management platform involves several steps. Below is a comprehensive guide to help you through the process:
- Select the Right Platform: Choose an IoT management platform that offers free SSH keys and aligns with your organizational needs.
- Generate SSH Keys: Use the platform's built-in tools to generate public and private SSH keys for each device.
- Configure Devices: Install the public key on the server and configure devices to use the private key for authentication.
- Test Connectivity: Ensure secure and stable connections between devices and the management platform.
- Monitor and Maintain: Regularly update keys and monitor device activity to maintain security.
By following these steps, organizations can effectively implement free SSH keys in their IoT ecosystems.
Enhancing Security with SSH Keys
SSH keys provide a higher level of security compared to traditional password-based authentication methods. They eliminate the risk of brute-force attacks and reduce the likelihood of unauthorized access. To further enhance security, organizations should adopt the following practices:
- Regular Key Rotation: Replace SSH keys periodically to minimize the risk of compromise.
- Access Control: Limit access to private keys and ensure only authorized personnel can manage them.
- Network Segmentation: Isolate IoT devices from other networks to prevent lateral movement in case of a breach.
- Monitoring and Auditing: Continuously monitor SSH key usage and conduct regular audits to identify potential vulnerabilities.
By implementing these measures, organizations can significantly bolster the security of their IoT systems.
Best Practices for Managing SSH Keys
Managing SSH keys effectively is crucial for maintaining the security of IoT ecosystems. Below are some best practices to consider:
Key Management
- Store private keys securely using hardware security modules (HSMs) or encrypted storage solutions.
- Document key usage and ownership to ensure accountability and transparency.
Policy and Compliance
- Develop and enforce policies governing SSH key usage and management.
- Ensure compliance with industry standards and regulations, such as GDPR and HIPAA.
Adhering to these best practices will help organizations maintain a secure and compliant IoT environment.
Scalability Considerations for IoT Systems
As IoT ecosystems grow, scalability becomes a critical consideration. IoT management platforms that offer free SSH keys must be able to handle increasing numbers of devices without compromising performance or security. Below are some factors to consider when scaling IoT systems:
- Device Provisioning: Automate the provisioning process to accommodate new devices efficiently.
- Load Balancing: Implement load balancing techniques to distribute network traffic evenly.
- Resource Allocation: Optimize resource allocation to ensure optimal performance under varying loads.
By addressing these considerations, organizations can ensure their IoT systems remain scalable and secure as they grow.
Cost Implications of Using Free SSH Keys
While free SSH keys eliminate licensing costs, there are other cost implications to consider. These include:
- Initial Setup Costs: Investing in hardware and software to support SSH key management.
- Ongoing Maintenance Costs: Allocating resources for key rotation, monitoring, and auditing.
- Training Costs: Providing staff with the necessary training to manage SSH keys effectively.
Despite these costs, the long-term savings and security benefits of using free SSH keys often outweigh the initial investment.
The Future of IoT Management Platforms
The future of IoT management platforms looks promising, with advancements in AI, machine learning, and blockchain technology set to revolutionize the industry. These innovations will enhance security, improve scalability, and provide deeper insights into IoT ecosystems. As organizations continue to adopt IoT solutions, the demand for platforms offering free SSH keys will only increase.
Looking ahead, IoT management platforms will likely integrate more advanced features, such as predictive analytics and autonomous device management, further simplifying operations and enhancing security.
Conclusion and Next Steps
In conclusion, IoT management platforms offering free SSH keys provide a cost-effective and secure solution for managing IoT ecosystems. By understanding the benefits, implementation strategies, and best practices outlined in this guide, organizations can make informed decisions about securing their IoT systems.
We encourage readers to take the following steps:
- Explore the top IoT management platforms mentioned in this article.
- Implement free SSH keys in your IoT ecosystem following the steps provided.
- Share your experiences and insights in the comments section below.
For more information on IoT management and security, visit our website and explore our other articles. Together, let's build a secure and connected future.