In today's interconnected world, finding the best SSH RemoteIoT free solutions has become essential for both individuals and organizations looking to secure their remote connections. With the rise of IoT devices and the need for secure access, understanding how SSH works and identifying free tools can significantly enhance your cybersecurity posture. Whether you're a developer, a hobbyist, or an IT professional, this guide will provide you with everything you need to know about SSH RemoteIoT free options.
SSH, or Secure Shell, is a cryptographic network protocol that facilitates secure communication between devices over an unsecured network. As more devices become part of the Internet of Things (IoT), the importance of secure remote access grows exponentially. This article will explore the best SSH RemoteIoT free solutions available, helping you choose the right tool for your needs.
From understanding the basics of SSH to exploring advanced features, we will cover everything step-by-step. By the end of this guide, you'll have a clear understanding of what SSH RemoteIoT free solutions can do for you and how to implement them effectively.
Read also:Mira Duterte Unveiling The Remarkable Journey Of A Rising Political Figure
Table of Contents
- Introduction to SSH RemoteIoT
- Benefits of Using SSH for RemoteIoT
- Best SSH RemoteIoT Free Tools
- How to Set Up SSH RemoteIoT
- Security Considerations for SSH RemoteIoT
- Comparison of SSH RemoteIoT Free Solutions
- Troubleshooting Common SSH Issues
- Use Cases for SSH RemoteIoT
- Future Trends in SSH RemoteIoT
- Conclusion
Introduction to SSH RemoteIoT
SSH RemoteIoT refers to the use of Secure Shell (SSH) protocols for managing and securing IoT devices remotely. This technology allows users to connect to IoT devices over the internet securely, ensuring that data transmission remains encrypted and protected from unauthorized access.
One of the primary advantages of SSH RemoteIoT is its ability to provide a secure channel for communication between devices, regardless of their physical location. This is particularly important for IoT devices, which are often deployed in remote or hard-to-reach areas.
Why SSH Matters for IoT Devices
SSH is widely regarded as one of the most secure methods for remote access. Its encryption capabilities ensure that sensitive data remains protected from cyber threats. Additionally, SSH supports authentication mechanisms that verify the identity of both the client and the server, further enhancing security.
- Encryption: SSH uses strong encryption algorithms to secure data in transit.
- Authentication: SSH supports various authentication methods, including passwords, public keys, and certificates.
- Portability: SSH is available on multiple platforms, making it easy to integrate with IoT devices.
Benefits of Using SSH for RemoteIoT
Using SSH for RemoteIoT offers several advantages that make it an ideal choice for secure communication. Below are some of the key benefits:
Enhanced Security
SSH provides robust security features, including encryption, authentication, and integrity checks. These features ensure that your IoT devices remain protected from unauthorized access and data breaches.
Scalability
SSH is highly scalable and can handle large volumes of data without compromising performance. This makes it suitable for use in large-scale IoT deployments where multiple devices need to be managed simultaneously.
Read also:Securely Connect Remote Iot P2p Ssh Download A Comprehensive Guide
Cost-Effective
Many SSH RemoteIoT solutions are available for free, making them an affordable option for individuals and small businesses. This eliminates the need for expensive proprietary software while still providing enterprise-level security.
Best SSH RemoteIoT Free Tools
Several free SSH RemoteIoT tools are available, each with its own set of features and capabilities. Below are some of the best options:
1. OpenSSH
OpenSSH is one of the most popular SSH tools available. It is open-source, highly customizable, and supports a wide range of platforms. OpenSSH provides robust security features and is widely regarded as the industry standard for SSH implementations.
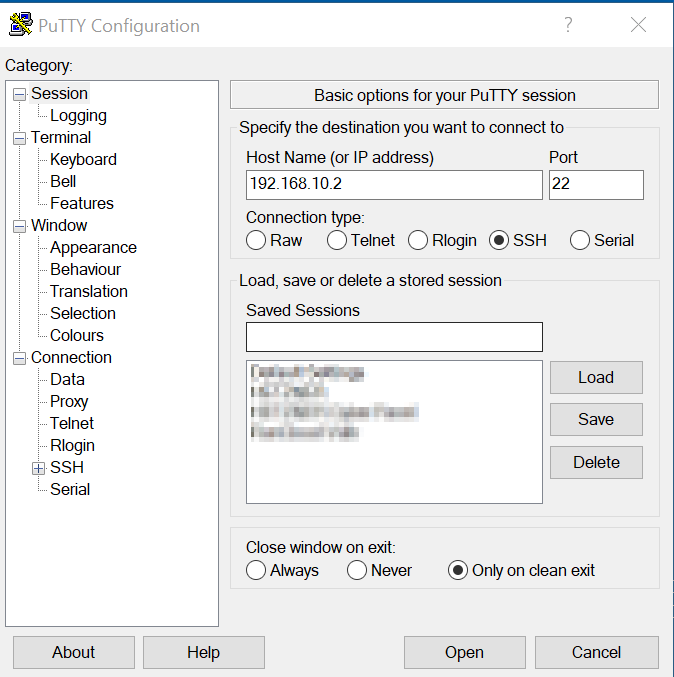
2. PuTTY
PuTTY is a free SSH client that is widely used on Windows platforms. It offers a simple interface and supports various protocols, including SSH, Telnet, and Rlogin. PuTTY is lightweight and easy to use, making it an excellent choice for beginners.
3. Bitvise SSH Client
Bitvise SSH Client is another popular free SSH tool that offers advanced features such as SFTP file transfer and tunneling capabilities. It is compatible with both Windows and Linux platforms and provides excellent performance and reliability.
How to Set Up SSH RemoteIoT
Setting up SSH RemoteIoT involves several steps, including configuring the server, generating keys, and establishing a connection. Below is a step-by-step guide:
Step 1: Install SSH Server
The first step is to install an SSH server on your IoT device. Most Linux-based systems come with OpenSSH pre-installed, but you may need to install it manually on other platforms.
Step 2: Generate SSH Keys
Generate SSH keys to enable passwordless authentication. This involves creating a public-private key pair using a tool like ssh-keygen.
Step 3: Configure SSH Settings
Once the server is installed and keys are generated, you can configure SSH settings to suit your needs. This includes setting up port forwarding, enabling specific users, and defining access restrictions.
Security Considerations for SSH RemoteIoT
While SSH provides robust security features, there are still some considerations to keep in mind to ensure maximum protection. Below are some best practices:
Use Strong Passwords
Ensure that all user accounts have strong, unique passwords to prevent unauthorized access. Avoid using default credentials or easily guessable passwords.
Enable Two-Factor Authentication
Two-factor authentication adds an extra layer of security by requiring users to provide a second form of identification, such as a one-time code sent to their mobile device.
Regularly Update Software
Keep your SSH server and client software up to date with the latest security patches and updates. This helps protect against known vulnerabilities and ensures optimal performance.
Comparison of SSH RemoteIoT Free Solutions
Choosing the right SSH RemoteIoT free solution depends on your specific needs and requirements. Below is a comparison of some of the most popular options:
| Tool | Platform | Features | Security |
|---|---|---|---|
| OpenSSH | Linux, macOS, Windows | Highly customizable, open-source | Strong encryption, public key authentication |
| PuTTY | Windows | Simple interface, supports multiple protocols | Basic encryption, password authentication |
| Bitvise SSH Client | Windows, Linux | SFTP support, tunneling capabilities | Advanced encryption, two-factor authentication |
Troubleshooting Common SSH Issues
Even with the best SSH RemoteIoT free solutions, issues can arise. Below are some common problems and their solutions:
Connection Refused
If you receive a "connection refused" error, it may indicate that the SSH server is not running or the port is blocked. Ensure that the server is properly configured and that any firewalls or routers are set up to allow SSH traffic.
Authentication Failed
Authentication failures can occur due to incorrect credentials or misconfigured settings. Double-check your username, password, and key files to ensure they are correct.
Slow Performance
Slow SSH connections can be caused by network issues or server overload. Try optimizing your network settings or upgrading your server hardware if necessary.
Use Cases for SSH RemoteIoT
SSH RemoteIoT has numerous applications across various industries. Below are some common use cases:
1. Remote Device Management
SSH allows IT administrators to manage IoT devices remotely, reducing the need for physical access and saving time and resources.
2. Secure Data Transfer
SSH provides a secure channel for transferring data between devices, ensuring that sensitive information remains protected during transmission.
3. Automation and Scripting
SSH can be used to automate repetitive tasks and scripts, improving efficiency and reducing the risk of human error.
Future Trends in SSH RemoteIoT
As the IoT landscape continues to evolve, so too will the role of SSH in securing remote connections. Below are some emerging trends to watch:
Quantum-Safe Encryption
With the rise of quantum computing, there is a growing need for encryption methods that can withstand attacks from quantum computers. SSH is likely to adopt quantum-safe algorithms in the future to ensure long-term security.
AI-Driven Security
Artificial intelligence and machine learning are increasingly being used to enhance cybersecurity. SSH may incorporate AI-driven features to detect and respond to threats in real-time.
Zero-Trust Architecture
Zero-trust architecture is becoming a popular approach to cybersecurity, where all users and devices must be continuously verified. SSH is well-suited to this model due to its strong authentication and encryption capabilities.
Conclusion
In conclusion, the best SSH RemoteIoT free solutions offer a secure, cost-effective way to manage and interact with IoT devices remotely. By understanding the basics of SSH and exploring the available tools, you can choose the right solution for your needs and implement it effectively.
We encourage you to share your thoughts and experiences in the comments section below. If you found this article helpful, consider sharing it with others who may benefit from the information. For more insights into cybersecurity and IoT, explore our other articles on the site.